Upgrading to TLS 1.2 using Cloudflare
August 3, 2023
NeetoCal is one of the products built under neeto. NeetoCal makes it easier to manage meetings. We wanted to allow users to use Zoom as one of the ways to have online meetings. We submitted the NeetoCal app for approval to the Zoom team. The Zoom security team notified us that they could not approve the app, because the app was supporting TLS 1.0 and TLS 1.1.
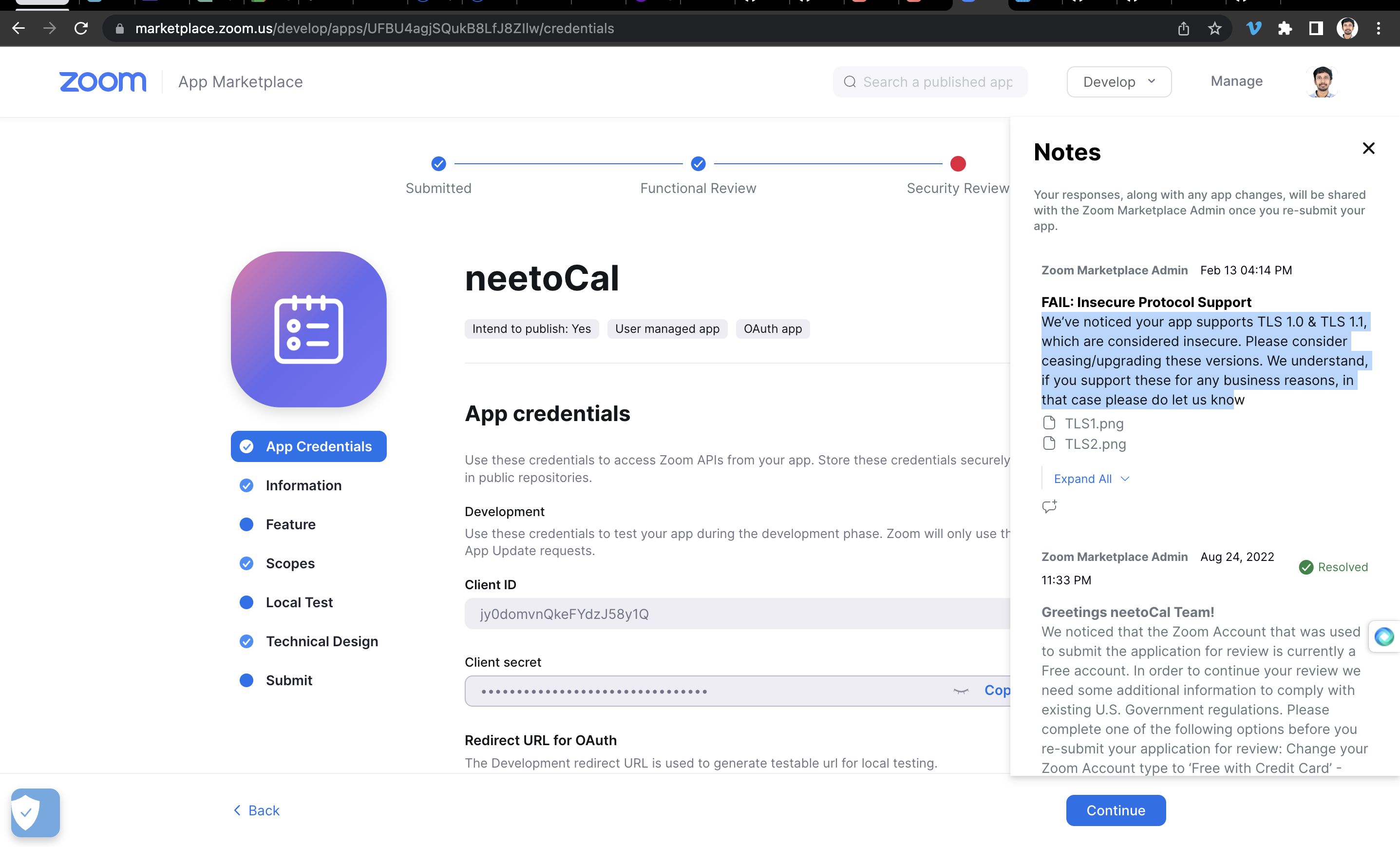
We checked with SSLlabs and it said the same thing: the servers support TLS 1.0
and TLS 1.1.
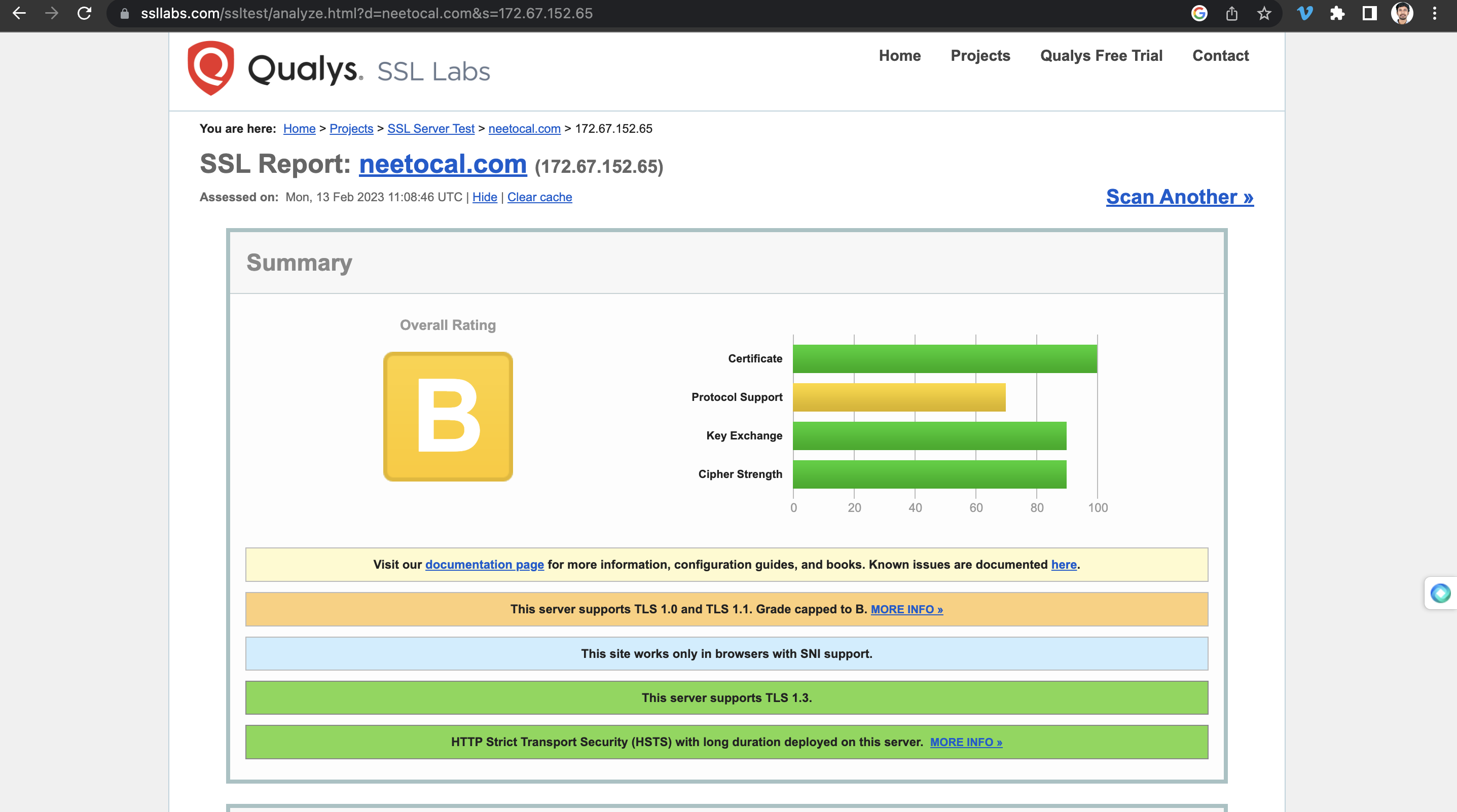
TLS 1.0 was published in 1999, and TLS 1.1 was published in 2006. Microsoft and other companies don't support these two versions of TLS. Even Heroku doesn't support it.
All our Neeto applications are hosted on Heroku. If Heroku doesn't support TLS 1.0 and TLS 1.1, how come the server supports these older versions of TLS?
Solving the TLS issue using Cloudflare
We use Cloudflare as our DNS server for all Neeto products. Cloudflare allows us to proxy the request. It means that when the user hits neetocal.com, their request is not going to Heroku. Cloudflare will intercept the request, and then Cloudflare will make a request to the Heroku server on behalf of the user. When Cloudflare makes this request to Heroku will use its own SSL certificate.
Cloudflare allows us to have control over the "Minimum TLS version" to support. We configured Cloudflare to not support TLS 1.0 and TLS 1.1.
The following video goes into step-by-step detail on how we configured this in Cloudflare.
CDN77 is the service we used in the video to check the TLS version.
Follow @bigbinary on X. Check out our full blog archive.